SLG1
Data Description
The SLG1 event is used in SAP to display application logs.
Potential Use Cases
This event could be used in the following scenarios:
Trend SLG1 error messages over time
Alert on specific error conditions
Display business document processing based on the data within the application
Metric Filters
The Metric Filter needs to be defined to extract data for this event. Log into the managed system and execute the /n/bnwvs/main transaction code. Then go to Administrator → Metric filters → SLG1 filter.
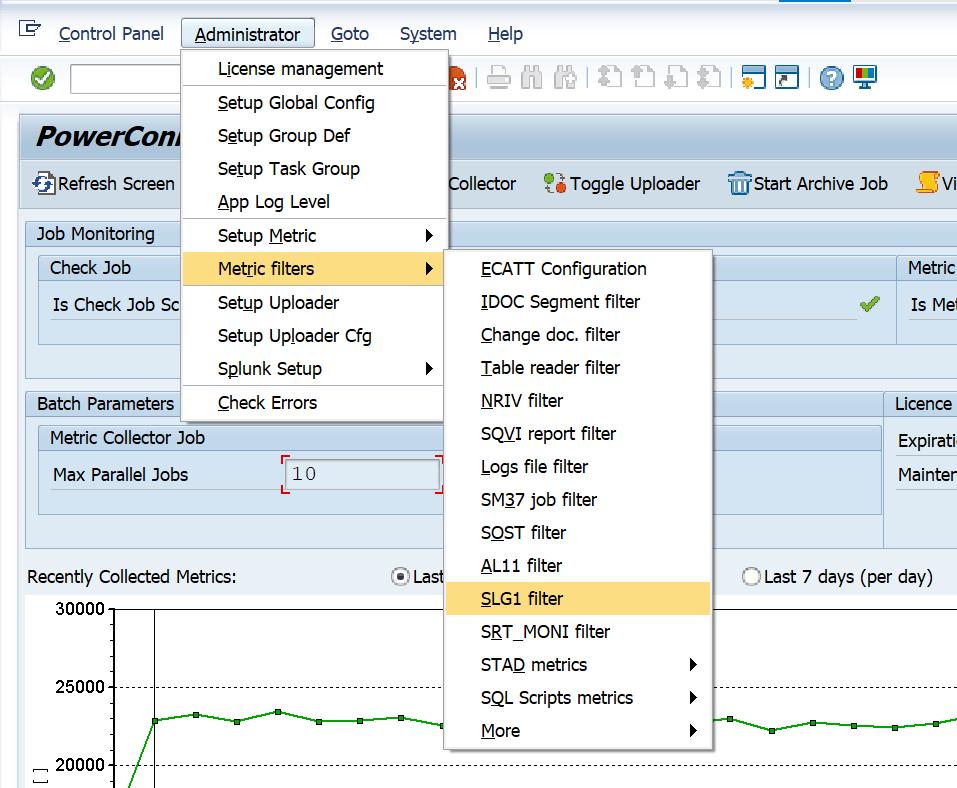
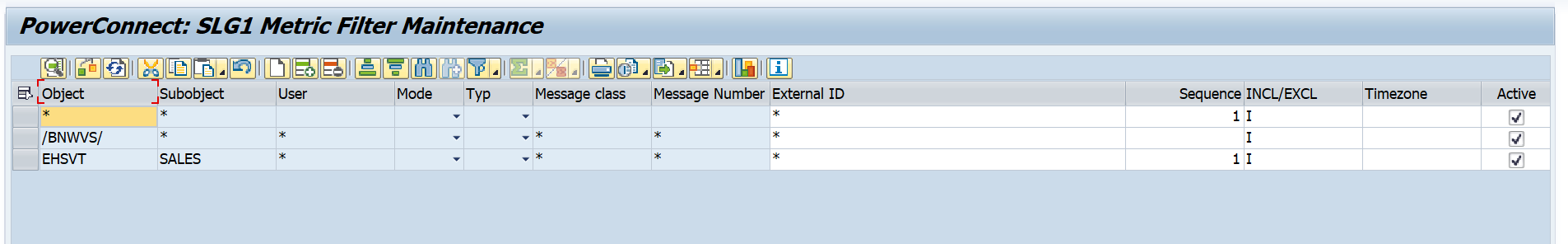
Then fill out the configuration based on your needs, and save. Below is a summary of the fields and their associated function:
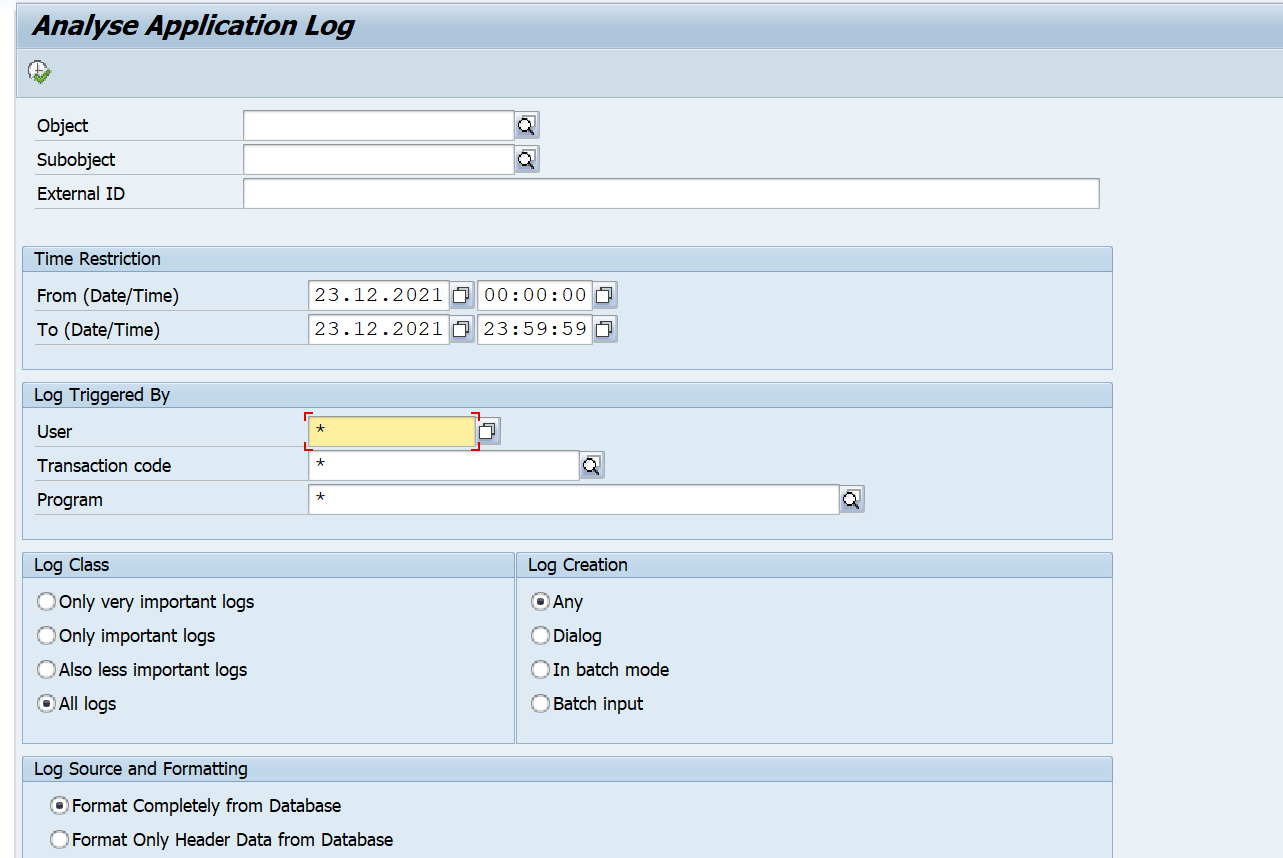
Object - This field represents the application log object name. If you would like to extract data from all objects, place a wildcard value in this field (not recommended based on potential data volume), or specify an object from the SLG1 transaction that you would like to extract.
Subobject - This field represents the application log object's subobject, and is associated with the object field. If you would like to extract data from all subobjects, place a wildcard value in this field, or specify a subobject from the SLG1 transaction that you would like to extract.
User - This field is the name of the user that caused the log event. If you would like to extract data from all users that caused the log event, place a wildcard value in this field, or specify a specific username from the SLG1 transaction.
Mode - This field corresponds to the Log Creation mode, which is how the log was created. The potential values are A = Any, D = Dialog, I = In batch mode, and B = Batch input. Leave this field blank if you want to extract all log creation modes, otherwise specify the desired value.
Typ - This field refers to the message type. The potential values are: A = Abend/Cancel, E = Error, W = Warning, I = Information, S = Success. Leave this field blank if you want to extract all message types, otherwise specify the desired value.
Message Class - This field refers to the message class. If you want to extract data from all message classes, place a wildcard value in the message class field, otherwise specify the desired value.
Message Number - This field refers to the message number. If you want to extract data from all message number, place a wildcard value in the message number field, otherwise specify the desired value.
External ID - This is an ID that can be assigned to a particular application program. If you want to extract all external IDs associated with the selection criteria, place a wildcard value in this field, otherwise enter the desired external ID value.
Sequence - This field is used to make a unique entry into the table if the key fields of Object, Subobject, User, Mode, Typ, Message Class, and Message Number are identical. This is a numeric field, so if there are identical entries based on the field value combination previously stated, enter a unique sequence number as seen above.
INCL/EXCL - This is an include/exclude flag. Otherwise, use an I to include the objects. If you want to exclude certain objects from being selected input an E
Timezone - This field is used if the SLG1 log is being written to a user timezone that is not the system timezone. This field is primarily used if the customer discovers data is not being collected. This field can be left empty if the system timezone is being used, otherwise specify the user timezone value.
Active - Select this box to enable the configuration. If you would like to disable the configuration uncheck the box.
Here is an example of what the SLG1 metric filter looks like when it is filled out:
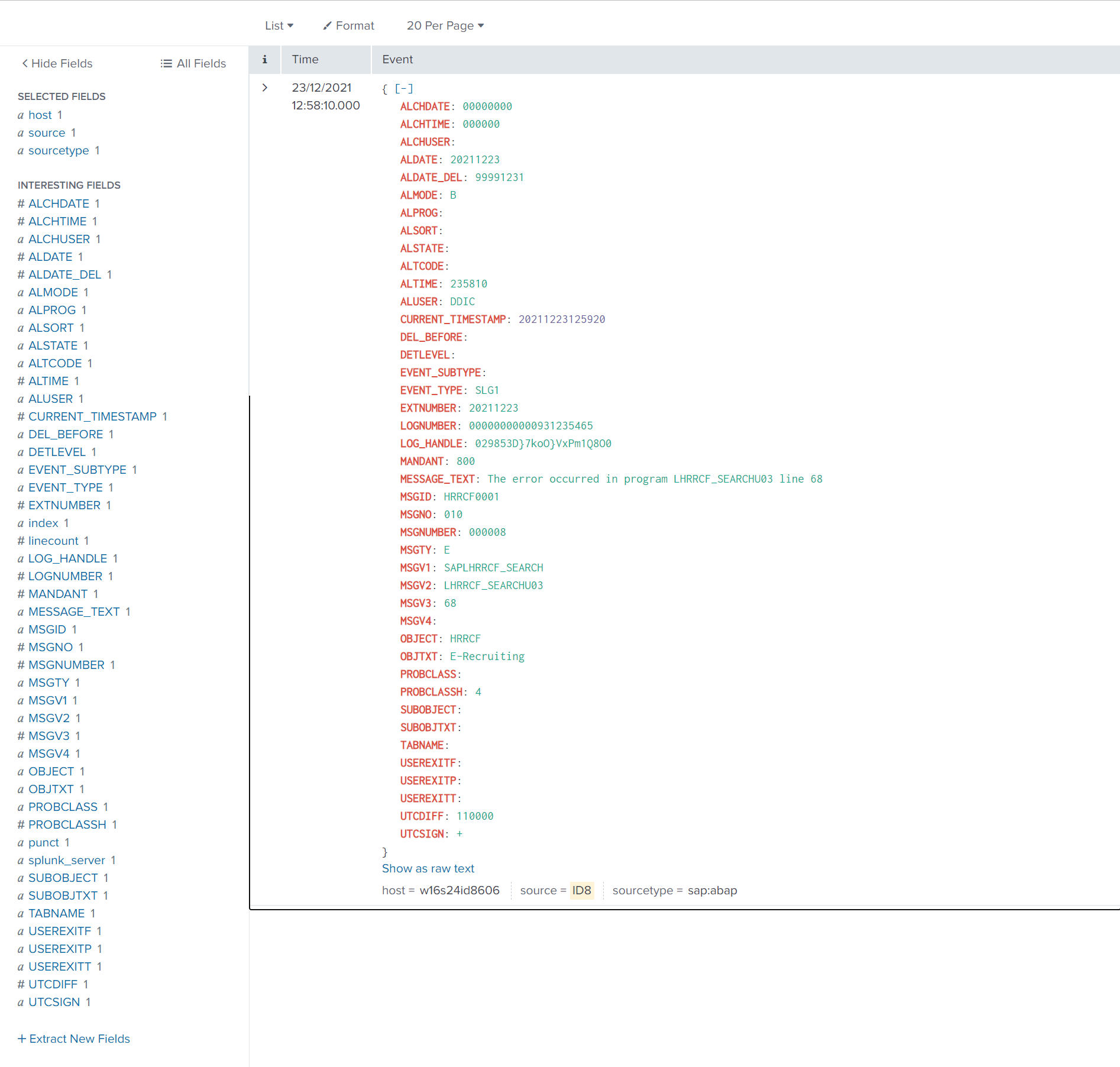
Splunk Event
Important Note: The Metric Filter needs to be configured to enable data extraction for this event.
The event will look like this in Splunk:
SAP Navigation
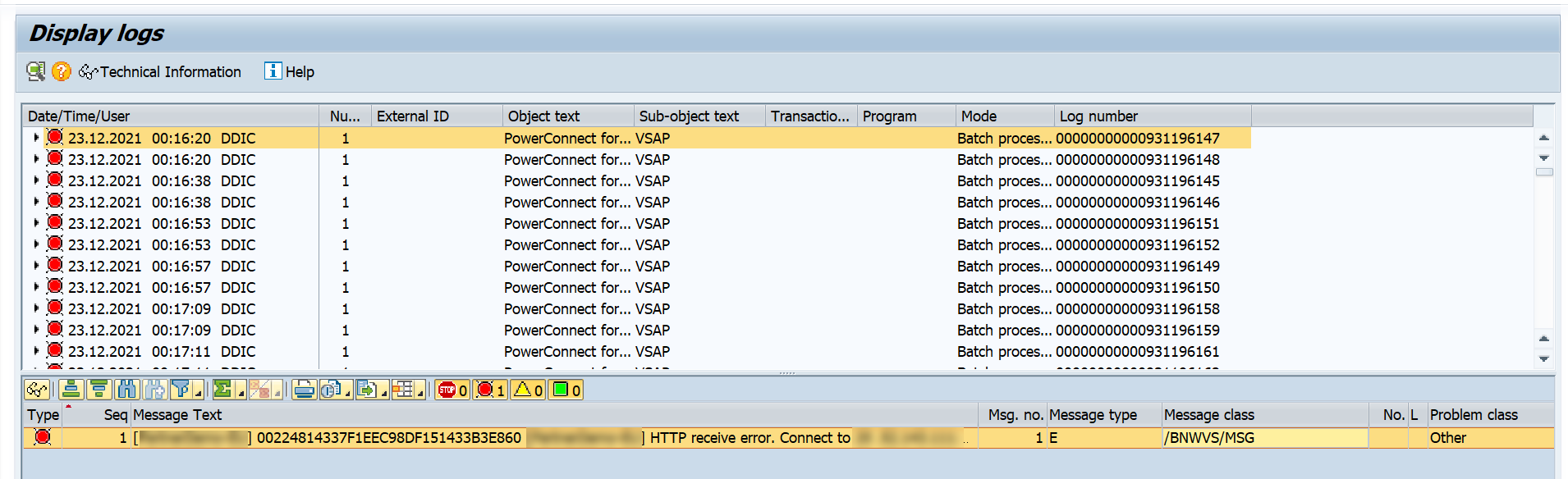
Navigate to this data by using the SLG1 t-code, and enter the desired selection criteria from the subsequent screen, and select the Execute button.
Click on a specific application log. The information displayed will match the data extracted and sent to Splunk by the PowerConnect application.