KB 237 - Extractor data in does not populate in System Analysis
KB 237 (Splunk): Extractor data in does not populate in System Analysis
Category: Problem | Priority: Normal |
|---|---|
Platform: Splunk | Version: 1 from 08.12.2025 |
Description
The extractor information does not populate correctly for the System Analysis view. You may be missing the description, frequency, and categories associated with the extractor, but the latest status and last event received should still be present.
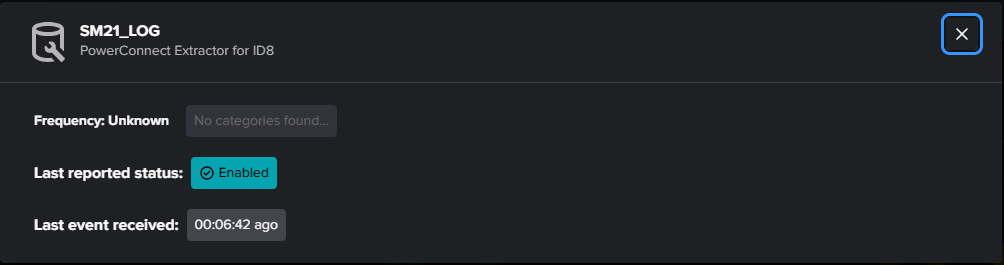
Cause
The search designed to populate this lookup runs but does not include the required outputlookup command for saving the information to be used by System Analysis.
Resolution
Please upgrade to PowerConnect Splunk app release 9.0.1. The manual solution to the issue can be found below.
Please append the following commands onto the saved search:
| rename source as sys_id ET as event_type CATEGORIES as categories DESCRIPTION as description
| table key sys_id event_type description categories frequency powerconnect_state last_status_time data_state last_received_time last_search_time
| outputlookup pc_extractor_data key_field=keyThe final search should be:
`sap-abap(GROUP_LIST,GROUP_DEF)` source="*" GROUP_DEF=*
| rename GROUP_DEF as ET
| eval powerconnect_state=if(ACTIVE=="X", "true", "false")
| `convert_seconds_to_human_readable_format(WAIT_PERIOD)`
| rename time_in_human_readable_format as Frequency
| stats latest(Frequency) as frequency max(_time) as last_status_time latest(powerconnect_state) as powerconnect_state by source ET CATEGORIES DESCRIPTION
| join ET source type=left
[ tstats latest(_time) as last_time where (`sap-index` source = "*" AND EVENT_TYPE="*") by source, EVENT_TYPE
| eval time_difference = now()-last_time
| `convert_seconds_to_human_readable_format(time_difference)`
| rename EVENT_TYPE as ET, time_in_human_readable_format as last_received last_time as last_received_time
| fields - formatted_dur]
| eval data_state = if(powerconnect_state=="true" OR last_received!="","true","false"),
last_search_time = now(),
key = source."_".ET
| fields - time_difference
| sort 0 key
| makemv delim="," CATEGORIES
| nomv CATEGORIES
| rename source as sys_id ET as event_type CATEGORIES as categories DESCRIPTION as description
| table key sys_id event_type description categories frequency powerconnect_state last_status_time data_state last_received_time last_search_time
| outputlookup pc_extractor_data key_field=keyProduct version
Product | From | To |
PowerConnect App for Splunk | 9.0.0 | 9.0.0 |
