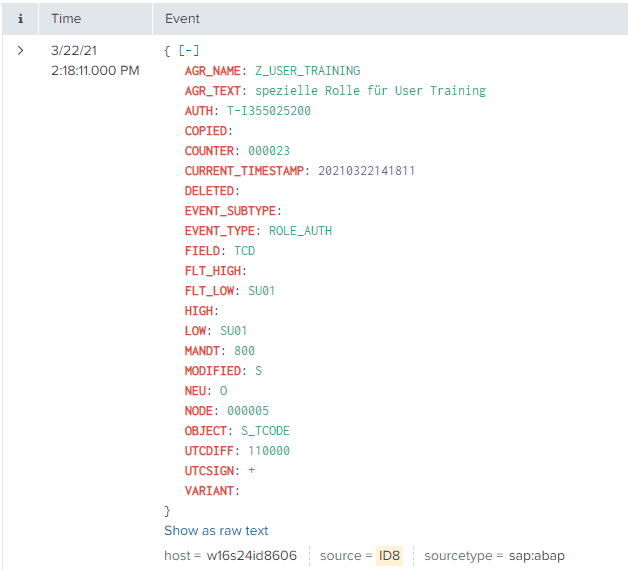
ROLE_AUTH
Data Description
The ROLE_AUTH event is used in SAP to view authorization objects associated with security roles.
Potential Use Cases
This event could be used for the following scenarios:
Determine if sensitive authorizations are being assigned to users
Evaluate whether there are sensitive combinations of authorization objects being assigned to users
Correlate the authorization object data with the data from SUIM to determine when the authorization object change took place
Metric Filters
To activate the collection of the authorization objects please complete the following steps log into the managed system, and execute the /n/bnwvs/main transaction.
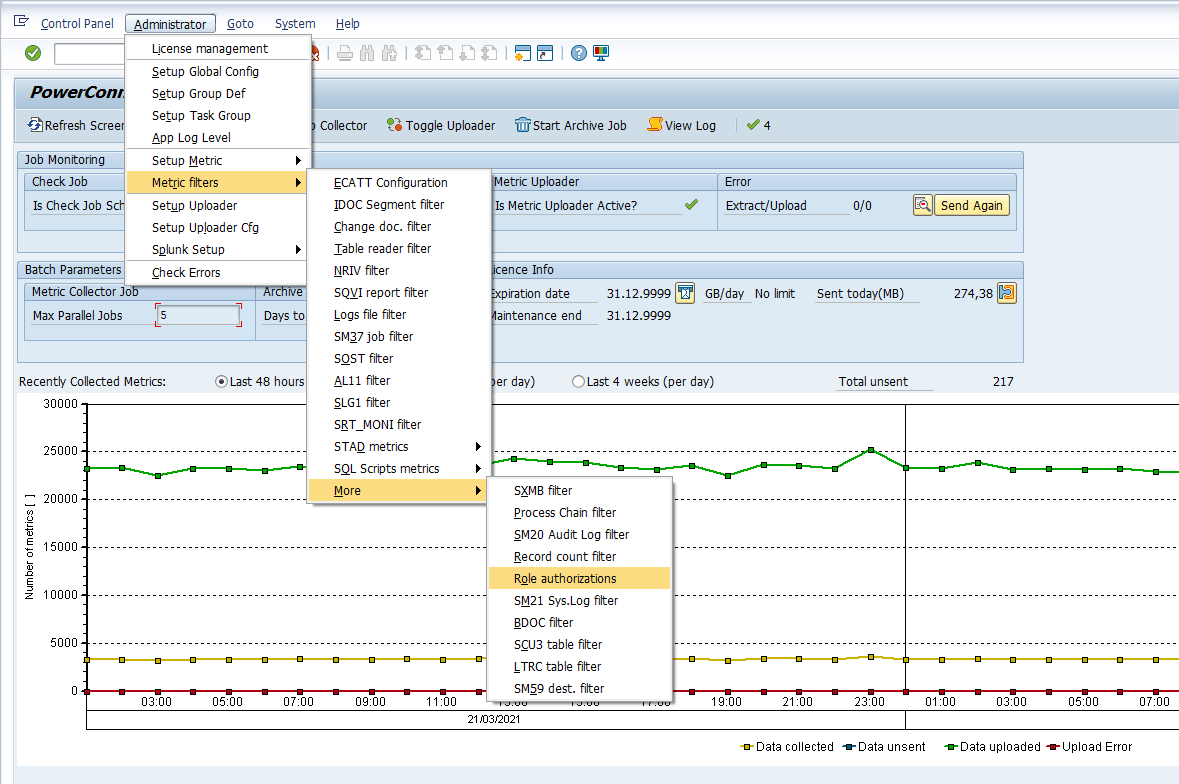
Then go to Administrator → Metric Filters → More → Role authorizations
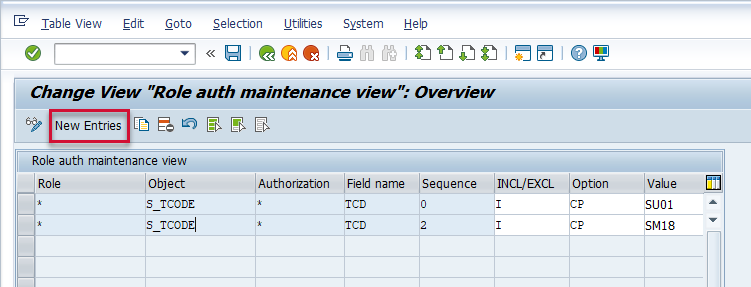
Once in the Role authorizations filter, select the “New Entries” button. Then place the string value for the role and authorization object details that you would like to collect the data for. Please note that wildcards are accepted.
Important Note: The ROLE_AUTH data can generate a significant amount of data in your system if you do not clearly specify the metric filters. Please be specific in the criteria you use in the filter.
Here are the fields from the filter:
Role - This is the role name for which the authorization object will be extracted for. If you would like the specific authorization object to be extracted for all roles input a wildcard. Otherwise, specify the roles for which you would like the authorization objects to be extracted for.
Object - This is the authorization object for which the data will be extracted. If you would like all authorization objects to be extracted input a wildcard. Otherwise, specify the authorization objects you would like to extract.
Authorization - This is the authorization name associated with the authorization configuration. If you would like all authorization names to be extracted input a wildcard. Otherwise, specify the individual authorization names you would like to extract.
Field name - This is the field name associated with an authorization. For example, a t-code is noted as TCD in AGR_1251.
Sequence - This field is used to make a unique entry into the table if the key fields of Role, Object, Authorization, and Field are identical. This is a numeric field, so if there are identical entries based on the field value combination previously stated, enter a unique sequence number as seen above.
INCL/EXCL - This is an include/exclude flag. Otherwise, use an I to include the objects. If you want to exclude certain objects from being selected input an E
Option - There are two field values which can be entered into this field:
CP – Is used to find all permissions, which includes defined value. So if you defined FLT_LOW=SM18, then it could find LOW=*
EQ – Is used for exact match. For instance if you would like to find permissions where LOW=SM18, and do not need those which have ‘*’. Or even if you need to find all ‘*’ permissions.
Value - These fields are used to define the range of objects that should be extracted. If you would like to extract all transactions between AL08 and SU01 alphabetically, you would input AL08 in the first value field and SU01 in the second value field.
Active - Select this box to enable the configuration. If you would like to disable the configuration uncheck the box.
Splunk Event
The event will look like this in Splunk:
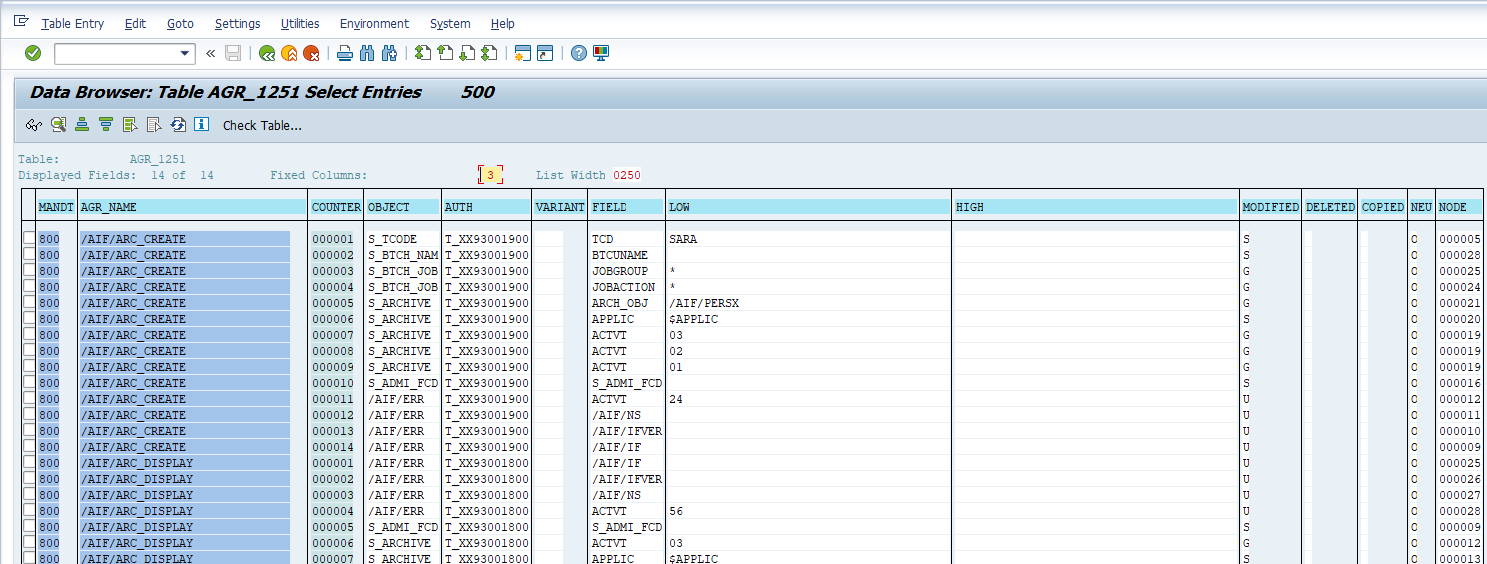
SAP Navigation
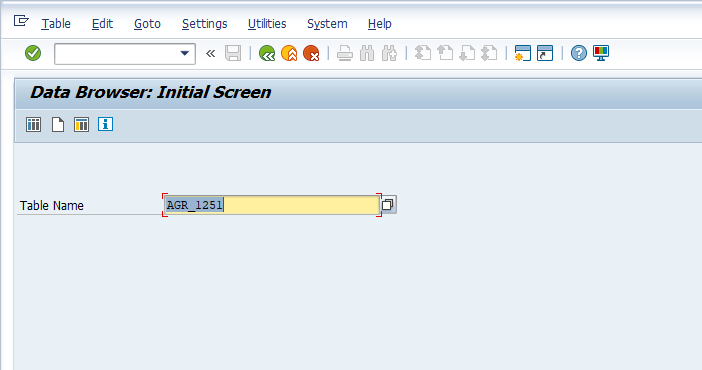
Navigate to this data by using the SE16 t-code and entering the value of AGR_1251 in the Table Name field. Hit the “Enter” key on your keyboard to proceed.
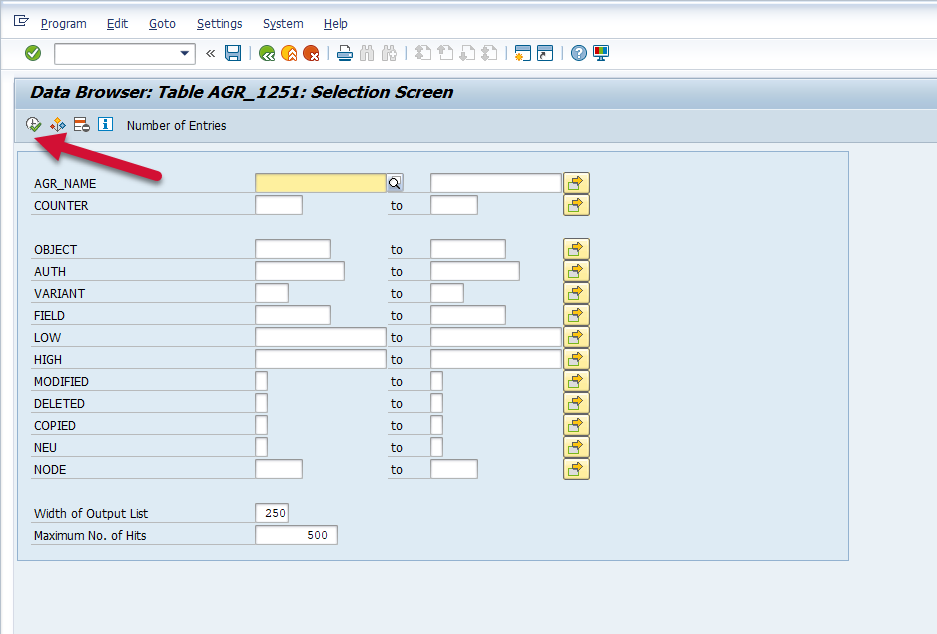
Enter the user-defined parameters for what you are looking for in the selection criteria. Then hit the “Execute” button.
The data will then be displayed, which will match the values in Splunk.